cWPA / WPA2加密高速破解的真相 第5頁|IT168 安全
WPA / WPA2加密高速破解的真相
這種採用了類似Rainbow Tables原理,通過Pre-Compute即預運算的方式,來進行提前運算以生成WPA-PSK加密Hash,從而建立起來的WPA-PSK Hash Tables,可以如事先設想般有效地大幅度提升破解效率。一般來說,可以將以前的100~~300 key/s的普通單機破解速率,提升到30,000~~100,000 key/s,提升了近300~~1000倍!!!這才是國內外無線黑客目前使用的破解技術,就一些地下組織而言,甚至個別秉持執著、探求本質精神的黑客通 過改進優化代碼等方式使得破解速率突破了150,000k/s,而且還有提升空間。這個速度意味著什麼,如果再換置成最新的硬件配置呢?聰明的你一定明 白。
下圖6即為在cowpatty裡對獲取的WPA握手包進行WPA Table破解界面,可以看到在導入Table之後,破解速率達到了6,5228 pass/second。
圖6 在Cowpatty裡進行WPA Tables破解界面
我想,對於很多無線用戶來說,這才是真正的噩夢。古希臘哲學家蘇格拉底曾說過這麼一句話: 「認識你自己。」 ,但實際上很多時候都是黑客背地猖獗,而很多
網絡及
安全管理人員要麼對攻擊者的技術僅是略知皮毛,要麼就根本一無所知,而且甚至不知道自己在經過所謂安全配置後的 網絡架構,將實際面臨什麼樣的風險。
雖然說公開一些技術也許反而會引起個別心懷惡意的人注意,不過出於對無線安全理念的普及及深入理 解,幫助很多已經完成或者正在進行無線網絡規劃的軍警政機構、大中型企業及特殊部門,更清楚地認識到無線網絡的風險,從而儘可能地完善自身的不足,避免不 必要的損失,才是本書的出發點。
當然,要說明的是,Tables的建立並沒有想像的那麼容易,就建立本身而言,其效率非常低下,加上需 要指定預攻擊AP的SSID,想要建立一套針對所有常見接入點,並採用簡單密碼的WPA-PSK Hash Tables,其生成文件佔據的
硬盤空間最少也要1~~3G。需要深入瞭解WPA Table的讀者,可以到這個名為The Church of Wifi的無線黑客組織瞭解更多內容,該組織官方站點為
http://www.churchofwifi.org,該組織在過去的兩年裡成功建立了龐大的 WPA Table庫,並將其簡化的WPA-PSK Hash Table版本提供
免費下載,對很多無線黑客而言,這確實是個福音,但遺憾的是,即便是簡化版本,其大小也已經超過了30G。
感興趣的 讀者可以到
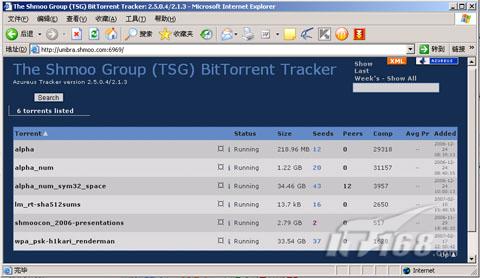
http://umbra.shmoo.com:6969去下載這個簡化版本的Table種子文件,該Table全部下載回來大小有
33.54GB,需要說明的是,生成該Table所依據的字典雖然經過黑客組織的篩選,但是由於國情不同,所以裡面部分內容可能並不適合國內情況的使用。 比如雖然都會有人使用姓名作為密碼,在國外可能是類似於BruceLee這樣的英文名稱,但是到了國內就可能是Lilianjie這樣的拼音了。
圖7 30G WPA Hash下載頁面
不過,對於無線網絡管理員,並不能因此鬆一口氣,真正的噩夢才剛剛開始,因為這個方法也同樣適用於破解WPA2加密。而且,國外一些地下高級黑客組織, 也已經建立了高達500G的詳盡WPA/WPA2攻擊Table庫,甚至一些基本完善的WPA-PSK Hash Tables已經在黑客網站上開始公開出售,只需要支付120美金左右,就會有8張包含WPA-PSK Hash Tables 的DVD光盤通過Fedex直接送到你的手上。
小D:由最後的說明,看出是字典法的改進,WPA安不安全見人見智…